Difference between revisions of "Flash Extraction"
Polymorphic7 (talk | contribs) m (href to yt vid.) |
Polymorphic7 (talk | contribs) m (flashrom added) |
||
| (11 intermediate revisions by the same user not shown) | |||
| Line 69: | Line 69: | ||
:* [https://en.wikipedia.org/wiki/1-Wire One-Wire] | :* [https://en.wikipedia.org/wiki/1-Wire One-Wire] | ||
::- 1-Wire is a wired half-duplex serial bus designed by Dallas Semiconductor that provides low-speed (16.3 kbit/s) data communication and supply voltage over a single conductor. | ::- 1-Wire is a wired half-duplex serial bus designed by Dallas Semiconductor that provides low-speed (16.3 kbit/s) data communication and supply voltage over a single conductor. | ||
| − | ::: Genuine Dell laptop power supplies use the 1-Wire protocol to | + | ::: '''[Example]''' Genuine Dell laptop power supplies use the 1-Wire protocol to transmit data over the third wire to the laptop's embedded controller, providing information about power, current, and voltage ratings. |
| − | ::: The | + | ::: The embedded controller then verifies that a compatible power supply is connected, allowing all VRM phases to operate at maximum duty cycle. |
::: Emulating the [https://github.com/orgua/OneWireHub/blob/main/examples/DS2502_DELLCHG/DS2502_DELLCHG.ino DS2502 TO-92-3 1-wire Dell charger ID EEPROM.] | ::: Emulating the [https://github.com/orgua/OneWireHub/blob/main/examples/DS2502_DELLCHG/DS2502_DELLCHG.ino DS2502 TO-92-3 1-wire Dell charger ID EEPROM.] | ||
| Line 82: | Line 82: | ||
=====External ROM===== | =====External ROM===== | ||
| − | : In case of an external | + | : In case of an external ROM you can always try to read it with a programmer and try to dump the contents this way for later static analysis. |
=====Internal ROM===== | =====Internal ROM===== | ||
| − | When your | + | When your target chip has a built-in ROM and the chip is locked you are out of luck trying to easily read the firmware in most cases.<br> |
| − | Here is | + | Here is where it comes handy to know of different methods widely used to attack these chips in order to retrieve the firmware for later static analysis or even live debugging. |
::* 1. Decapsulation | ::* 1. Decapsulation | ||
:::- [https://www.youtube.com/watch?v=T1rRgb9N9s4 '''RECESSIM video:''' Nitric Acid and Microscopes. Decapsulating IC's.] | :::- [https://www.youtube.com/watch?v=T1rRgb9N9s4 '''RECESSIM video:''' Nitric Acid and Microscopes. Decapsulating IC's.] | ||
::* 2. Bootloader hacking | ::* 2. Bootloader hacking | ||
| − | :::;- [https://0xinfection.github.io/reversing/reversing-for-everyone.pdf Great resources on | + | :::;- [https://0xinfection.github.io/reversing/reversing-for-everyone.pdf Great resources on reverse engineering] |
::* 3. Fault injection & Glitching Attacks | ::* 3. Fault injection & Glitching Attacks | ||
:::;- VCC glitching (Crowbar Circuits) | :::;- VCC glitching (Crowbar Circuits) | ||
| Line 118: | Line 118: | ||
======Atmel SAM4C32 Glitching (Crowbar Circuit)====== | ======Atmel SAM4C32 Glitching (Crowbar Circuit)====== | ||
| − | + | : > [[:ATSAM4C32|Full in-depth wiki page can be found here.]] | |
| − | |||
| − | [[ | ||
| − | |||
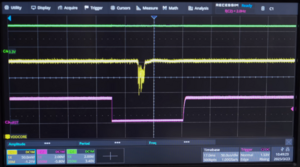
| − | ====Debugging Tools==== | + | : Atmel SAM4C32 reset low period during early start-up process somewhere in the bootloader showing vulnerable time for glitch.<br> |
| + | : After glitching the chip, JTAG comes online serving a command prompt which allows to dump the firmware of the chip protected by Atmel's Security Bit Feature called GPNVM.<br> | ||
| + | : [[File:Atmel SAM4 series glitch.png|none|thumb|Atmel SAM4C32 glitching. Yellow VDDCORE, Purple RST..]] | ||
| + | : Credits to [https://www.0x01team.com/hw_security/bypassing-microchip-atmel-sam-e70-s70-v70-v71-security/ 0x01 Team] and [https://www.youtube.com/watch?v=IOD5voFTAz8 RECESSIM] for finding the reset low period being connected to the glitch timebase. | ||
| + | |||
| + | ====Debugging==== | ||
| + | =====Debugging Hardware / Tools===== | ||
::* Tools that are used to find debug ports, OCD interfaces, serial port I/O. | ::* Tools that are used to find debug ports, OCD interfaces, serial port I/O. | ||
| − | + | ::;- [https://github.com/openocd-org/openocd OpenOCD (Open On-Chip Debugger)] | |
| − | + | ::;- [https://www.picotech.com/products/oscilloscope PicoScope. The modern alternative to the traditional benchtop oscilloscope.] | |
| − | + | ::;- [https://buspirate.com/ BusPirate - universal bus interface device for I2C and SPI.] | |
| − | + | ::;- [https://github.com/travisgoodspeed/goodfet GoodFET JTAG adapter] | |
| − | + | ::;- [https://mouser.com/new/segger/seggerjlink/ J-Link In-Circuit Debugger] | |
| − | + | ::;- [https://github.com/grandideastudio/jtagulator JTAGulator is an open source hardware tool that assists in identifying OCD interfaces from test points, vias, component pads, or connectors on a target device.] | |
| + | |||
| + | =====Logic Analyzer===== | ||
| + | :: [https://hardwear.io/netherlands-2024/speakers/sasha-sheremetov.php hardwear.io - Hacking NAND Memory Pinout using Logic Analyzer.] | ||
| + | :: '''Abstract:''' | ||
| + | :: This presentation is about analysis of technological pinout of NAND memory in such devices as microSD, eMMC and other monolithic chips using a logic analyzer. | ||
| + | :: YouTube video: https://www.youtube.com/watch?v=sgl9Sfu79Lc | ||
====Non-intrusive methods==== | ====Non-intrusive methods==== | ||
| Line 163: | Line 172: | ||
:::; <pre style="font-weight: normal;">Signing an OTA update package involves applying a digital signature using cryptographic methods. This process serves several critical purposes. 1. Authenticity. 2. Integrity.</pre> | :::; <pre style="font-weight: normal;">Signing an OTA update package involves applying a digital signature using cryptographic methods. This process serves several critical purposes. 1. Authenticity. 2. Integrity.</pre> | ||
| − | ====Programmers & Nand Flash Controllers ==== | + | ====Programmers / Flash Utilities & Nand Flash Controllers ==== |
=====Programmers===== | =====Programmers===== | ||
======SOP16 / 8 / VSOP8 / WSON8 / PDIP8 / SO8 / TSSOP8 / UFDFPN8====== | ======SOP16 / 8 / VSOP8 / WSON8 / PDIP8 / SO8 / TSSOP8 / UFDFPN8====== | ||
| Line 170: | Line 179: | ||
:: ➤ Ezp2023+ programmer with appropriate SOP16 SOP8 adapter | :: ➤ Ezp2023+ programmer with appropriate SOP16 SOP8 adapter | ||
:::;- '''Important note:''' limited NOR Flash and NAND Flash support! Might need 1.8v adapter, buggy software. [https://www.onetransistor.eu/2023/12/how-to-use-ezp2023-usb-programmer.html Read more here.] | :::;- '''Important note:''' limited NOR Flash and NAND Flash support! Might need 1.8v adapter, buggy software. [https://www.onetransistor.eu/2023/12/how-to-use-ezp2023-usb-programmer.html Read more here.] | ||
| + | =====Flash Utilities===== | ||
| + | :: ➤ flashrom (Support: SPI/BIOS/EC) | ||
| + | :::;- [https://github.com/flashrom/flashrom flashrom] - is a utility for identifying, reading, writing, verifying and erasing flash chips. It is designed to flash BIOS/EFI/coreboot/firmware/optionROM images on mainboards, network/graphics/storage controller cards, and various other programmer devices. | ||
=====Nand Flash Controllers===== | =====Nand Flash Controllers===== | ||
Listing of nand flash controller interface chips & off the shelf hardware (cheap stuff).<br> | Listing of nand flash controller interface chips & off the shelf hardware (cheap stuff).<br> | ||
| − | Since the search engine is broken @ the usual suspects. I use a search query | + | Since the search engine is broken @ the usual suspects: DHgate, Gearbest, Banggood, Aliexpress or various other China stores. I use a search query for example '''“TSOP48 usb pcb controller flash disk site:aliexpress.com”''' in image search mode. |
======BGA-153====== | ======BGA-153====== | ||
:: ➤ ['''UFS'''] JMicron JMS901 USB 3 (single channel nand supported) | :: ➤ ['''UFS'''] JMicron JMS901 USB 3 (single channel nand supported) | ||
| Line 190: | Line 202: | ||
====The final chapter ==== | ====The final chapter ==== | ||
| − | Analyzing dumped data. | + | Analyzing dumped data. You might also find the [[Software_Tools#|software category interesting.]] |
| − | ::* | + | ::* Analyzing & unpacking firmware blobs |
:::;- [https://github.com/onekey-sec/unblob Unblob] | :::;- [https://github.com/onekey-sec/unblob Unblob] | ||
:::;- [https://github.com/ReFirmLabs/binwalk Binwalk] | :::;- [https://github.com/ReFirmLabs/binwalk Binwalk] | ||
| Line 198: | Line 210: | ||
:::;- [https://github.com/attify/firmware-analysis-toolkit Firmware Analysis Tools (FAT)] | :::;- [https://github.com/attify/firmware-analysis-toolkit Firmware Analysis Tools (FAT)] | ||
:::;- [https://github.com/fkie-cad/FACT_core FACT (Firmware Analysis and Comparison Tool)] | :::;- [https://github.com/fkie-cad/FACT_core FACT (Firmware Analysis and Comparison Tool)] | ||
| + | |||
| + | ::* Disassemblers | ||
| + | :::;- [[Software_Tools#Interactive_Disassemblers_.28static_analysis.29|Interactive Disassemblers (static analysis)]] | ||
Revision as of 21:02, 30 June 2025
Contents
Table
Introduction
Embedded devices or smart devices store their code in a ROM or flash memory chip primarily because these types of memory are non-volatile and permanent even after power loss.
The data is stored even after the system is turned off in contrast to volatile memory that needs to stay powered on. A prime example of this is if you put your computer in hibernate S4 or (modern standby) S0.
The RAM memory will stay powered to keep everything in the memory active so that if you press the power button the system will be back up in seconds, if you disconnect the power the hibernated session will be gone because RAM is volatile memory.
This wiki page will provide a basic explanation of embedded and smart devices and their ways of storing code in modern electronics and provide some great resources in regard of the extraction techniques.
Some in-depth information regarding the subject will be shared here too.
Purpose of data extraction
Reverse engineering code stored in ROM firmware is a practice that serves multiple purposes across various fields, particularly in technology and security.
One of the primary reasons for reverse engineering firmware is to identify and mitigate security vulnerabilities. As IoT devices and embedded systems become more prevalent, ensuring their security is crucial. By analyzing the firmware, security researchers can uncover weaknesses in the code that could be exploited by malicious actors locally or even remotely which could pose a high risk to many users.
Below, we will explore the reasons why individuals and organizations engage in this process.
- Security audits
- - White hats - good guys, safeguarding systems & data to prevent hackers from getting in.
- - Grey hats - in between good and bad.
- - Black hats - abusing vulnerabilities to earn money or do damage, or other illicit services.
- Industrial hardware repair
- - Repair shops
- - Technical department in a company doing repairs locally
- Recovery in mission critical failure mode (back-up a day keeps the Dr away)
- - Data recovery companies
Physical locations
- Chip Internal ROM (embedded inside the microcontroller most often also known as a SoC system-on-a-chip)
- Chip external ROM (an external part on the PCB)
Types of Memory
- Various types of EEPROMs
- Serial EEPROM
- Parallel EEPROM
- Flash Memory -> Bigger, faster and cheaper but less reliable (less write cycles)
- NAND/NOR Flash
- FeRAM
Chip interfaces
- Also known as general-purpose ports (GPIO).
- - Bit-banging is the process of emulating a protocol in software instead of relying on a hardware peripheral to do the same things.
- - I2C is a two-wire serial communication protocol using a serial data line (SDA) and a serial clock line (SCL).
- The protocol supports multiple target devices on a communication bus and can also support multiple controllers that send and receive commands and data.
- Pinout
- VCC (1.5V up to 5V)
- SCL (I2C Clock)
- SDA (I2C Data)
- GND (Ground)
- The protocol supports multiple target devices on a communication bus and can also support multiple controllers that send and receive commands and data.
- - SPI is a synchronous, full duplex main-subnode-based interface.
- The data from the main or the subnode is synchronized on the rising or falling clock edge. Both main and subnode can transmit data at the same time.
- The SPI interface can be either 3-wire (Single SPI mode), 4-wire (Dual SPI mode) or 6-wire (Quad SPI mode).
- Pinout Dual SPI mode
- MOSI (Master Out Slave In)
- MISO (Master In Slave Out)
- SCLK (Serial Clock)
- SS/CS (Slave Select)
- - A parallel I/O port is a mechanism that allows the software to interact with external devices. It is called parallel because multiple signals can be accessed all at once.
- Microwire, often spelled μWire, is essentially a predecessor of SPI and a trademark of National Semiconductor.
- It's a strict subset of SPI: half-duplex, and using SPI mode 0. Microwire chips tend to need slower clock rates than newer SPI versions; perhaps 2 MHz vs. 20 MHz.
- Some Microwire chips also support a three-wire mode.
- - The QSPI peripheral provides support for communicating with an external flash memory device using SPI.
- - 1-Wire is a wired half-duplex serial bus designed by Dallas Semiconductor that provides low-speed (16.3 kbit/s) data communication and supply voltage over a single conductor.
- [Example] Genuine Dell laptop power supplies use the 1-Wire protocol to transmit data over the third wire to the laptop's embedded controller, providing information about power, current, and voltage ratings.
- The embedded controller then verifies that a compatible power supply is connected, allowing all VRM phases to operate at maximum duty cycle.
- Emulating the DS2502 TO-92-3 1-wire Dell charger ID EEPROM.
Programming
- In-circuit programming
- Allows programmable devices, such as microcontrollers, to be programmed while they are installed in a complete system, facilitating firmware updates without removing the chip.
- Out-of-circuit programming
- Refers to the process of programming microcontrollers or integrated circuits while they are removed from their final application circuit, typically using specialized programming equipment.
Extraction Methods [ >> hot topic << ]
External ROM
- In case of an external ROM you can always try to read it with a programmer and try to dump the contents this way for later static analysis.
Internal ROM
When your target chip has a built-in ROM and the chip is locked you are out of luck trying to easily read the firmware in most cases.
Here is where it comes handy to know of different methods widely used to attack these chips in order to retrieve the firmware for later static analysis or even live debugging.
- 1. Decapsulation
- 2. Bootloader hacking
- 3. Fault injection & Glitching Attacks
- - VCC glitching (Crowbar Circuits)
-
- RECESSIM video: Hacking into a Locked Microchip - Reverse Engineer shows you how it's done.
- Example paper 1. Fault Injection using Crowbars on Embedded Systems.
- Example paper 2. Injecting Software Vulnerabilities with Voltage Glitching.
- Example paper 3. Glitch it if you can: parameter search strategies for successful fault injection.
- Example paper 4. The Forgotten Threat of Voltage Glitching: A Case Study on Nvidia Tegra X2 SoCs
- - Clock glitching (Oscillator Circuits)
-
- Example paper 1. Ultra Freezing Attacks and Clock Glitching of Clock Oscillator Circuits
- Example paper 2. High Speed Clock Glitching
- Example paper 3. Glitching Demystified: Analyzing Control-flow-based Glitching Attacks and Defenses
- Example paper 4. Attacking Glitch Detection Circuits
- Example paper 5. Machine Learning-Based Detection of Glitch Attacks in Clock Signal Data
- - EMFI (Electromagnetic Fault Injection)
-
- Example paper 1. Electromagnetic fault injection using transient pulse injections a comparison of EM-FI and optical-FI on smart cards
- Example paper 2. Electro Magnetic Fault Injection
- Example paper 3. Exploring Effects of Electromagnetic Fault Injection on a 32-bit High Speed Embedded Device Microprocessor
- Example paper 4. Electromagnetic fault injection: the curse of flip-flops
- 4. Scanning Electron Microscopy (SEM)
- - An expensive method.
- ResearchGate - FinFET architecture under a E-beam (SEM).
- Public Fault Injection Toolkits
- - ChipWhisperer
- - PicoEMP
Atmel SAM4C32 Glitching (Crowbar Circuit)
- Atmel SAM4C32 reset low period during early start-up process somewhere in the bootloader showing vulnerable time for glitch.
- After glitching the chip, JTAG comes online serving a command prompt which allows to dump the firmware of the chip protected by Atmel's Security Bit Feature called GPNVM.
- Credits to 0x01 Team and RECESSIM for finding the reset low period being connected to the glitch timebase.
Debugging
Debugging Hardware / Tools
- Tools that are used to find debug ports, OCD interfaces, serial port I/O.
- - OpenOCD (Open On-Chip Debugger)
- - PicoScope. The modern alternative to the traditional benchtop oscilloscope.
- - BusPirate - universal bus interface device for I2C and SPI.
- - GoodFET JTAG adapter
- - J-Link In-Circuit Debugger
- - JTAGulator is an open source hardware tool that assists in identifying OCD interfaces from test points, vias, component pads, or connectors on a target device.
Logic Analyzer
- hardwear.io - Hacking NAND Memory Pinout using Logic Analyzer.
- Abstract:
- This presentation is about analysis of technological pinout of NAND memory in such devices as microSD, eMMC and other monolithic chips using a logic analyzer.
- YouTube video: https://www.youtube.com/watch?v=sgl9Sfu79Lc
Non-intrusive methods
[Vector] Factory debug / programming ports
- JTAG (primarily used for testing and debugging electronic circuits)
- - Finding a unpopulated or populated JTAG port on the PCB.
- UART (an asynchronous serial communication protocol that transmits data)
- TTL
- TTL defines voltage levels in digital logic circuits
[Vector] Network based [over-the-air (OTA) programming]
- Network stack - > WLAN / BT firmware bugs (OSI layer 1. physical)
- - Example 1. Broadcom Wi-Fi SoC remote heap overflow CVE 2017-0561
- - Example 2. Qualcomm Wi-Fi stack based buffer overflow CVE-2022-33279
- - Example 3. node-bluetooth remote buffer overflow CVE-2023-26110
- Network stack - > Promiscuous mode eavesdropping
- Promiscuous mode eavesdropping is needed to audit software code because it allows the monitoring of all network traffic, enabling auditors to detect
- unauthorized data access and vulnerabilities that may not be visible through standard monitoring methods.
Promiscuous mode eavesdropping is a network monitoring technique where a network interface card (NIC) captures all packets on the network segment, regardless of their destination address. This allows authorized or unauthorized users to intercept sensitive data transmitted over the network.
- Network stack - > MiTM (Man-in-the-middle) methods
- - SSL stripping
-
- Mitmproxy is your swiss-army knife for debugging, testing, privacy measurements, and penetration testing.
- Exploitation of Trust by OSI layer 7 local client modifications to do cert pinning (local pentesting).
- Github example click here.
- Local - > Cryptographic checksums
- A cryptographic checksum is a mathematical value generated by a cryptographic algorithm to verify the integrity of data, ensuring that it has not been altered during transmission or storage.
Not only are OTA updates after being downloaded over TCP+TLS by a device cryptographically checked to make sure the authenticity and integrity is accounted for, if this was not the case it could install a malicious update or simply brick million of devices. TCP already ensures data integrity through checksums and error detection mechanisms so by adding even more checks it's redundance is high.
- Local - > Signed updates
- A cryptographic signed package is a digital package that includes a cryptographic signature, ensuring the package’s authenticity, integrity, and origin from a trusted entity.
- This signature verifies that the package has not been altered since it was signed.
Signing an OTA update package involves applying a digital signature using cryptographic methods. This process serves several critical purposes. 1. Authenticity. 2. Integrity.
Programmers / Flash Utilities & Nand Flash Controllers
Programmers
SOP16 / 8 / VSOP8 / WSON8 / PDIP8 / SO8 / TSSOP8 / UFDFPN8
- ➤ CH341A programmer
- ➤ Ezp2023+ programmer with appropriate SOP16 SOP8 adapter
- - Important note: limited NOR Flash and NAND Flash support! Might need 1.8v adapter, buggy software. Read more here.
Flash Utilities
- ➤ flashrom (Support: SPI/BIOS/EC)
- - flashrom - is a utility for identifying, reading, writing, verifying and erasing flash chips. It is designed to flash BIOS/EFI/coreboot/firmware/optionROM images on mainboards, network/graphics/storage controller cards, and various other programmer devices.
- ➤ flashrom (Support: SPI/BIOS/EC)
Nand Flash Controllers
Listing of nand flash controller interface chips & off the shelf hardware (cheap stuff).
Since the search engine is broken @ the usual suspects: DHgate, Gearbest, Banggood, Aliexpress or various other China stores. I use a search query for example “TSOP48 usb pcb controller flash disk site:aliexpress.com” in image search mode.
BGA-153
- ➤ [UFS] JMicron JMS901 USB 3 (single channel nand supported)
- ➤ [eMMC] Alcor Micro AU6438 USB 2.0 (single channel nand supported)
TSOP48
- ➤ Innostor IS917 click here for details (Flash-extractor library)
- ➤ Silicon Motion Sm3281n click here for details (Flash-extractor library)
- ➤ Chipsbank CBM2099E click here for details (Flash-extractor library)
Nand Controller firmwares & datasheets
USBDev.ru is a great resource.
The final chapter
Analyzing dumped data. You might also find the software category interesting.
- Analyzing & unpacking firmware blobs
- Disassemblers