ATSAM4C32
Contents
Bypassing Microchip Atmel SAM4C32
Introduction
This write-up will cover analysis of the Microchip (ATMEL) SAM4C32 microcontroller vulnerability that allows an attacker to gain unlocked JTAG access to a previously locked device. This attack appears to affect many devices (though not all) in the SAM family. It was discovered that essentially the same attack performed by 0x01 Team on the SAM E70/S70/V70/V71 works on many SAM processors. What's novel about this write-up is identification of the Reset pin as a side channel.
While the attack method used was voltage fault injection, I believe EMFI (electromagnetic fault injection) could also be a viable method to bypass security. EMFI generally permits attacks without the need to remove all the capacitors on the power rail. This is helpful when attacking devices where you don't want to alter the target board.
Why attack the SAM4C32?
The SAM4C32 is used in this Landis+Gyr Generation 5 smart meter. I have a long history analyzing various aspects of these smart meters, previously extracting the firmware from a Generation 4 smart meter which uses a Renesas (Mitsubishi) M30626FHPGP processor. It is a M16C architecture and the extracted firmware proved challenging to reverse engineer with tools like Binary Ninja and Ghidra.
ARM architecture is supported by more RE (reverse engineering) tools and has been analyzed by more people in the RE community. Therefore, I decided to extract the firmware from the SAM4C32 to further my analysis of smart meter technology.
Locking Mechanism
The SAM4C32 makes use of general-purpose non-volatile memory (GPNVM) bits to control locking, boot mode and memory plane selection as seen below.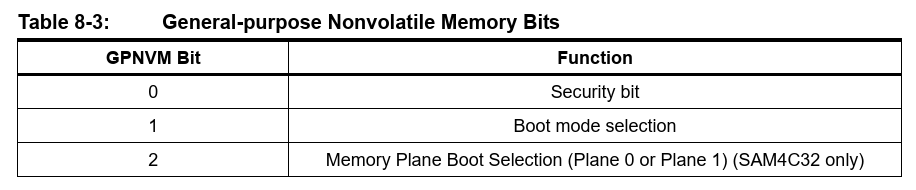 Below is extracted from Microchip datasheet DS60001717B.
Below is extracted from Microchip datasheet DS60001717B.
Security Bit
The SAM4C features a security bit based on a specific General-purpose NVM bit (GPNVM bit 0). When the security is enabled, any access to the Flash, SRAM, core registers and internal peripherals, either through the SW-DP/JTAG-DP interface or through the Fast Flash Programming Interface, is forbidden. This ensures the confidentiality of the code programmed in the Flash.
This security bit can only be enabled through the command “Set General-purpose NVM Bit 0” of the EEFC User Interface. Disabling the security bit can only be achieved by asserting the ERASE pin at 1, and after a full Flash erase is performed. When the security bit is deactivated, all accesses to the Flash, SRAM, Core registers, Internal Peripherals are permitted.
SAM-BA Boot
The SAM-BA Boot is a default Boot Program for the master processor (CM4P0) which provides an easy way to program in-situ the onchip Flash memory. The SAM-BA Boot Assistant supports serial communication via the UART0 or USB Port for the SAM4C32.
The SAM-BA Boot provides an interface with SAM-BA Graphic User Interface (GUI).
The SAM-BA Boot is in ROM and is mapped in Flash at address 0x0 when GPNVM bit 1 is set to 0.
Reset vs Power Cycle
TBD
Reset Pin as a Side Channel
TBD
Voltage Fault Injection
TBD
JTAG Access
TBD
Other Vulnerable Devices
TBD
Conclusion
TBD